A rapid shift has occurred over the years with information and rights management. With the introduction of the major cloud platforms, it’s theoretically never been easier to avoid the risk of producing and controlling hard copy information, by transitioning to a strictly soft copy data model. However, whether you’re implementing access controls that secure data use or planning a secure migration of data to the cloud, it can be a minefield to define the value and impact upon the information involved. To adequately protect this critical business asset, information value needs to be defined and mapped across physical and logical boundaries.
In this blog, Senior Information Security Consultant Simon Discombe delves into the concepts of information rights management (IRM) and how it holds the keys to controlling business data.
My experiences of information control across countless businesses have seen a significant range and subsequent shift over time in management techniques – not all of them good. Methods often range from flawed or unpredictable processes to absurdly complex accounting for non-sensitive information.
Setting aside specific techniques, it’s important to note that IRM refers to the various often automated methods that seek to control access to protected information or data. Digital rights management (DRM) on the other hand tends to refer to the control of mass-produced media through some similar technical means.
Beginning with the data owner, and flowing down to the data user/processor, IRM (when enabled) consistently enforces pre-set rights to access, modify, copy, print or share data. When IRM is ineffective, it may point to issues with the underlying control or guidance for information creation or collection, imposed by the data owner.
What is the value of your data?
Where to start in controlling data always remains the same, whether it’s personal information, business data, publicly available information, or classified material, understand what you have first. Initial questions to understand what you have, include:
- Who is the source or data owner?
- Are there any handling instructions?
- Is the data labelled in any way?
- Who or what is the data subject?
- What is the intended use of the data?
- How is the data valuable to the business?
Once answered, you can clarify what the classification (or sensitivity) is in order to provide effective handling of information in a manner that reflects its value. This is where classification schemes come in handy as they underpin IRM by grouping similar data types and stating expected controls.
Classifications are often business specific but can be standardised where they meet the aims of the business, for instance if a business supports a government entity, it may subscribe to the classifications of the relevant government classification scheme. More often than not though, private entities will classify information by privacy and confidentiality needs set by the business, its regulators, and its partners.
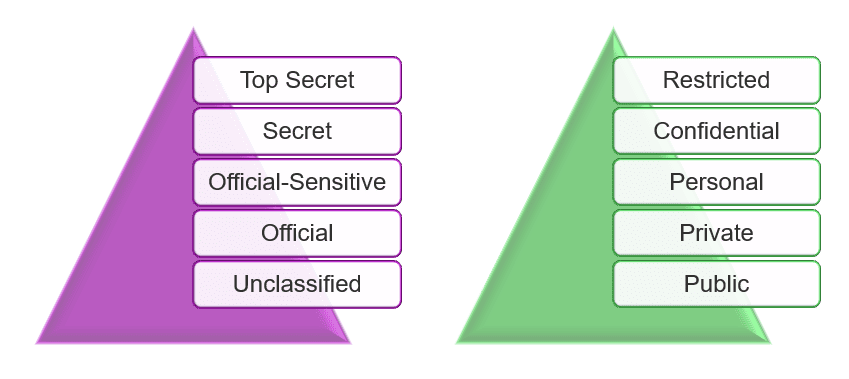
Formalised around the business’ selected classification scheme, there should be a clear policy that defines the classification levels, sets out key roles and responsibilities for data, and directs the use of classified business data. Otherwise known as a Classification and Handling Policy.
If you’re reading this and wondering why we are stuck in the past with ‘paper policies’, then it is important to remember that automation delivers against an established process or set of rules. Without a specific policy and classification scheme in place, automated IRM tools simply won’t deliver the expected outcome.
Make it easy to move your sensitive data
Once we have classified a piece of information, the next step is to find out where it exists and label it. Labelling is a key protection control, as data becomes tagged in a way that indicates its classification and handling requirements to users. Labels can be enforced manually though filenames, footnotes, and watermarking in documents or in more technical attributes such as metadata that can traverse multiple system and service types.
To ensure consistent control of data, these labels need to have a level of permanence that prevents removal by simple techniques such as deletion. Persistent labelling enables protections to remain with the information, scanning activities to capably map where certain data types are, and indicate sensitivity of information to users and external recipients.
With added complexities such as geographical distribution, virtualised instance replication, mass information augmentation of AI large language models (LLMs) and information optimisation, the use of information is more widespread than ever and requires a firm understanding of how these factors affect key business processes. Therefore, labelling plays a critical role when trying to define and apply controls to data flowing across systems, services, users, and third parties involved in accessing or processing business information.
Movement of information will also involve differentiating between where something is and where it is being used, in other words its geographic physical and logical (technological) storage locations. Technical issues from IRM compatibility across logical boundaries and existing infrastructure, and jurisdictional hurdles from data centre sites can otherwise adversely impact the effectiveness of business data control.
Understanding data protection
The development of a classification and handling scheme supported by labelling can be a time consuming and often neglected part of information security. Some departments or teams can become confused or uncooperative with new data protection requirements as they fear it might interfere with productivity.
If you need a helping hand to start, our experienced Advania consultants stand ready to support you in your journey from education to implementation of data protection schemes.
IRM techniques and tools
With a classification scheme defined and labels applied, IRM can begin to address some of the previously clunky and time absorbing work. Using the classification levels alongside organisational access control mechanisms, such as Microsoft’s EntraID governance and file-based discretional access control rules, IRM solutions help administrators and data owners to apply the correct information rights to users.
To be effective, IRM design deployments should typically consider five main business objectives as a minimum:
- Established account rights that describe the list of authorised actions for users against information assets and how these rights can be set, applied, altered, and revoked.
- Possible encryption methods to ensure that those without authorisation to conduct actions against information assets are prevented from interacting with them.
- Business policies as with classification and handling policies, will dictate the rules that direct what can and can’t occur with business assets, for example a Top-Secret document may not be permitted to move across logical storage areas and IRM will enforce these rules in a technical manner.
- Rights provisioning within the IRM solution itself will be critical to ensure that it supports the business objectives for managing role-based access and security groups as a broad scale activity, and whether or not low-level rights provisioning will be achievable.
- Information accessibility should be understood including the type of technology and cloud service models in use and how users are permitted to create, access, view, edit, copy, print, delete and forward the IRM protected business information. Additionally, the method used to identify and authenticate users and devices accessing IRM protected information, whether through local or domain joined services, such as certificates and licenses should be capable of integrating with the IRM solution.
With these implementation elements considered, whatever IRM solution has been selected, the full spectrum of features should now be achievable such as:
- File/object-level access control
- Trainable classifiers
- Prevention of unauthorised copying
- Persistent control internally and externally for the data lifecycle
- Real time policy alteration to allow change
- Expiration of access and retention
- Access history accounting
- Effective rights revocation
With these functions in place, testing of rulesets or ‘IRM policies’ can commence to ensure that migration from hard copy archives to soft copy data archiving will assure data protection through persistent technical controls. Businesses can use the available features of encryption, labelling, and rights control to apply strategic objectives to tactical user-level controls consistently no matter where the data is accessed from. This reduces not only the administrative burden on data owners but also reduces the uncertainty in housing high-value high-risk information.
Why it’s important to keep your data secure
The case for IRM is only getting stronger as the information environment becomes more regulated by legislation, standards, and frameworks. Just as businesses need to be aware of risks to their devices that they use daily to access business resources, access to information needs to be seen as just as, if not more, important to the protection of the company.
With fines for the improper protection of personal data now reaching into the billions as recently seen with Meta, it should become more apparent than ever that information is valuable. The ability to harvest data from social media sites to use in impersonation scams and social engineering attacks is only increasing in sophistication allowing for more genuine looking AI scams and phishing attacks. The dumping of exfiltrated data is becoming exceedingly damaging to the reputation of targeted businesses and the data subjects involved, and everyone must play their part in providing due care to the data in their care.
A well-defined information lifecycle, like any other asset management lifecycle, when implemented from start to finish can bring benefits, including:
- Quicker support to business requirements
- Secure sharing that prevents data loss
- Improved productivity and efficiency
- Removal of data siloes
- Business tailored security and compliance
- Improved risk management by effective tracking and accounting
- Increased value to products and service offerings
- Support to legal and regulatory requirements
In terms of work by vendors, Microsoft has capitalised upon many of its offerings to provide a seamless integration between rights management services (RMS), access controls from domain management tools such as EntraID, and Microsoft Purview services such as sensitivity labelling, scanning and trainable classifiers to support governance. However, other vendors are available with AWS and Google Cloud having some features available through their ‘Attribute-Based Identity and Access Management’, and ‘Sensitive Data Protection’ services respectively.
This exemplifies the positioning of IRM as a critical element in the information lifecycle that works with your environment to scale the effectiveness of controls that have been applied in the past to bring data security into the future.
Delivering change at scale
IRM can prevent many of the issues of the day that seek to derail information security, such as information sprawl, high-risk AI information ingestion, insecure sharing, and data loss. While risk is a tolerable part of doing business, the cost of getting things wrong with data may not be.
Working on information management takes time to discover what you have, where it is, plan for change, and be able to deliver change that doesn’t impact business output. Integration issues with key services, identity platform mapping errors, software installation and local legal complexities can all delay efforts. By getting any of the structural design wrong, data can be left behind and IRM can quickly become an expensive and ineffective tool.
Breaking the steps of IRM down into Discovery, Assessment, Implementation and Monitoring phases with the thread of Business Adoption running through all phases, positive changes in information management can be delivered. This provides a considered approach to managing the trove of data you are tasked with securing and ensures that the efforts conducted are measured effectively.
How quickly can we set up?
If you want to know how easy it would be to bring your information management controls in line with your business objectives, one of the best ways is to review your policies. Using policies, access control standards and handling instructions to bear against the data you hold will reflect how joined up your processes are. The more complex your technology or attack surface is, the more likely that there will be more work to do to integrate IRM effectively.
Talk with our experts today to find out how we can help in your journey to assuring that your data is well protected.