Identity and Access Management (IDAM) solutions have come a long way in providing centralised control to IT administrators by integrating various systems and services, but effective governance throughout the IDAM lifecycle is vital for defending assets effectively over time.
In this blog, Senior Information Security Consultant Simon Discombe, discusses what is IDAM, including practices that can guide the provision of authorised access to specified assets.
Identity is an exceptionally powerful key. Your voice, your name, and your data are just some of the factors that are part of your unique identity, which becomes critical for gaining trusted access to sensitive resources. Whether it’s for business or personal matters, having a unique identity linked to protected accounts, resources, or systems makes everyone a potential target of fairly unsavoury actors. By understanding how identities are created, delivered, and maintained, we can find ways to prevent access abuse.
What is IDAM?
Identity and Access Management, often termed as IDAM or IAM, refers to the process of granting, monitoring and removing access to data or systems against a unique identity. The foundations of IDAM will typically be supported by the secure application of four main objectives, known as AAA: Identity control, Authentication factors, Authorisation of rights, and Accounting for activity.
While these foundations are often thought of in technical terms, it’s important to understand that controlling physical access to sites and business assets is central to effective security – the theft of a poorly secured device may be all that is required to breach a network.
IDAM solutions should consist of the following features:
- Identity proofing using evidence-based registration
- Crafting unique identities related to a data subject or service
- Creating identity-based accounts
- Tying identities to devices
- Applying access control models to secure user-object rights
- Monitoring the lifecycle of accounts to review and revoke rights
Before continuing, it’s important to be aware that there a variety of IDAM terms that often relate to the same thing. For example, ‘users’, ‘entities’ and ‘subjects’ are all used to describe ‘a validated identity such as a service or person with rights to access business objects or resources on a system or network’. In this blog, I’ll refer to all identities as users.
Establishing users and authentication
Identification is the first step to defining a new user. Typically part of a new starter’s onboarding process, this should focus on a set of requirements to establish a new user and their validity on company systems. This is often termed user registration and involves identity proofing, whereby a new staff member will provide trustworthy documentation such as a driving licence to prove that they are who they say they are. Once documents are reviewed, the user is then provided with a unique identity on the company’s systems and authentication credentials can be configured and bound to the identity.
Where a new service is being registered, identity proofing is not often necessary and therefore privileged account users are the control point of these new ‘users’ and their associated credentials. Therefore, businesses should also consider how key services and their accesses are managed as with any other kind of user.
By all accounts, the individuality and sometimes even the obscurity of a user identity adds to the overall security of accounts by allowing distinction for activities and mitigating trivial brute force enumeration of account details. But users must also be reminded that their unique identification, such as username or email address, should not be shared as this exposes one half of a set of valid credentials.
Authentication methods
When planning authentication methods for the business, evaluate the types of devices and physical access required to authenticate to the network. Factoring in the security profile required for user devices and connection methods such as via VPNs or through a HTTPS connection will help to determine what authentication measures and strength are needed to keep local and remote staff communications secure.
While authentication methods differ, the three most commonly deployed authentication factors configured in order for systems to validate users involve:
- something a user knows (such as a password or PIN)
- something a user possesses (such as an access card or token)
- something a user is (a biometric trait)
Two other forms of user authentication that are used less often, and typically less secure, include:
- something a user does (such as a pattern-based code or typing cadence)
- somewhere a user is (via IP or GPS data)
Context-aware authentication adds a further layer to authentication, focusing on the more modern principles of zero trust. This method applies granular access control based on attributes expressed by a user and device at the time of the access request. Factors reviewed will involve cross-checking user identity, location, IP address, device type, device security compliance and time of access to provide a risk-based decision on whether to allow access based on company security policies.
When considering passwords and the configuration of multi-factor authentication (MFA), controls should be aligned to the business direction first and foremost leveraging best practices from reputable vendors and guidance bodies such as the UK’s National Cyber Security Centre, where applicable. Controls may include password complexity requirements, security MFA authenticator app usage and biometric authentication types.
The robustness of the user authentication process that is selected has a direct and correlated effect on the level of security of its accessible assets. Weaknesses or flaws in authentication measures can make unauthorised access trivial, for example the use of single factor password authentication can make it trivial for attackers to conduct brute force password guessing. Additionally, if authentication methods aren’t strong enough, it can rightfully cast doubt upon whether an individual even conducted actions on a user account.
Whichever way you choose to establish valid identities or authenticate users, access controls must consider identity and authentication measures and how they will interact with authorisation and accounting controls to support ongoing security aims. Augmenting IDAM designs with zero trust principles will ensure that once inside the network, activity conducted by users is expected and aligned to the business’ risk appetite and its policies.
Authorising permissions
Assuming that a user has succeeded in presenting valid access credentials, how can a business make sure that actions conducted by that user are limited to those activities expected as part of the user’s role? Applying the least amount of privilege needed and role-based access rights are great places to start. This will ensure that from onboarding, users are not instantly trusted to access all of a network’s most sensitive resources and conduct unlimited actions such as creating, viewing, modifying, sharing, and deleting objects. These rights should be considered as part of the new starter process previously mentioned that is often supported or controlled by HR.
Within a new starter process, much of the application of rights will be based on existing templates for department role holders, line manager discretion, approval of HR personnel, and approvals by IT administrators that deliver the user credentials. However, if there is a breakdown or lack of process in this area, the effectiveness of the IDAM process as a whole will start off in a poorly managed state as authorised rights for users may contradict the intent of company policies.
IT administrators are often the most influential people in this process being able to review whether or not rights seem overly permissive or provide excessive access, but this requires clear collaboration between teams to establish what is expected. Using well-crafted role templates based on a baseline of least privilege rights can often provide effective management – but again must be reviewed and updated according to changing needs.
IDAM solutions
Looking at the market today there are a variety of IDAM tools ready for businesses to leverage to manage their user attack surface. From Active Directory service providers supporting centralised access control and user management to the likes of single sign on (SSO), Federated Identity Management (FIdM) and Privileged Identity Management (PIM), there are plenty of technical tools to draw upon. Other controls such as Information Rights Management (IRM) can also provide automated and granular rights provisioning to prevent errors occurring at the authorisation stage.
Bear in mind that with all of these solutions there are risks and benefits in their adoption. Some can offer more native tailored features that amplify your security efforts and alleviate the cost and burden associated with identity and access management.
Before taking on a solution, consider whether it can be implemented effectively and the impacts upon users and business processes. Testing of technical security policies related to access control (e.g., acceptable use, conditional access, and account management), before wider deployment will often address problems before they arise. These policies should also seek to support subject matter experts in applying principles of split control, zero trust, least privilege, and need-to-know when designing technical solutions.
Confidence in user management
Developing or improving the way in which a business manages its users is essential for ensuring appropriate access control is being enforced across business assets in the manner expected. Whether the need is to build out a new secure process for identity creation and management, or assisting in the overhaul of an old process and technical solutions that require positive change, experienced Advania Consultants can help deliver. From setting strategy to implementing technical designs, Advania has a range of solutions to support your objectives.
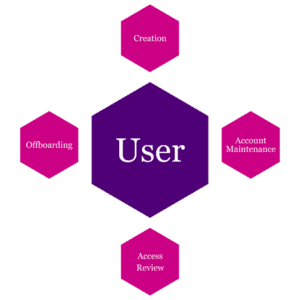
The IDAM lifecycle
Just like any business-as-usual process, security controls are never truly finished. Milestones established in a lifecycle assist with ongoing management, and there is even one for IDAM.
Using a similar approach to asset management, the IDAM lifecycle should focus on the provisioning of accounts all the way through to the decommissioning of them.
Creation
As referred to with identity registration and authentication configurations, creation focuses on the secure onboarding of a new user, considering:
- how they will be enrolled
- their identity proved
- credentials and hardware issued
Prior to providing users with access credentials, this stage can also be the point at which companies request acceptance of users regarding acceptable use policies that describe acceptable activity, issue reporting and monitoring. Further policies and training should also direct new users at this point forward as to the technical requirements of their continued use of devices and the network.
Account maintenance
This involves support for users as they navigate the company’s network and services including further rights provisioning based on role-based needs, service desk requests regarding user errors, and internal staff movements.
Internal staff changes and rights provisioning should mirror the secure nature of provisioning rights for new starters undergoing approvals and change management to prevent negative security impacts.
Access reviews
These should be conducted at a pre-set interval especially for privileged accounts, sensitive asset access rights, and internal staff moves. Without effectively monitoring access rights, least privilege principles become undermined and the potential for privilege creep and abuse can often occur and go undetected. To ensure insider risks are proactively managed, valid access must be evaluated, including whether accounts are required anymore, especially service accounts.
Offboarding
This activity should form the end of the line for many accounts, disabling access and revoking rights from users. Of course, the easiest way to deprovision accounts is to delete them. However, in doing so the business may also remove critical access to linked resources required for business processes. Disabling accounts and access, especially during terminations, may therefore provide a more controlled method for the business in deprovisioning allowing the business to evaluate the account before subsequent removal. For security purposes, these accounts must be removed after a suitable time to avoid the account being targeted for exploitation.
Whilst many elements make up the broad adoption of the IDAM lifecycle, it is important to have visibility of all of the various moving parts within account control, often achieved through leveraging the collaborative expertise of your internal stakeholders and technical tooling. By following a robust lifecycle, common processes can be implemented quicker, more securely and with more confidence in success of overall identity management.
Accounting and accountability
Accounting for a user’s behaviour on a network is critical in enforcing accountability for actions. During the lifecycle, and even after the deprovisioning of accounts, businesses will require a solution that allows for monitoring and linking of actions to users in order to sometimes reverse those actions or highlight them. By deploying auditing, monitoring, and logging tools to the business environment, activity can be recorded and reviewed to trace events and their corresponding user.
Logs that are actually required to hold users accountable will vary across risk appetite, system types and services but should be specified in company governance such as policies and standards that meet security aims. Recording all logs for the sake of monitoring will reduce security efforts and not be targeted enough to provide for effective review. Focusing on critical systems, privileged access and security-controlled events will provide more efficient insight to when and where network activity is impacting the business.
The ability to provide reliable logs is based on the ability to provide robust identification and authentication methods, as well as secured logs that resist malicious alteration. Monitoring data should therefore record events related to users in a central and protected location that prevents tampering with data and erasure of activity logs.
Threats to Identity and Access Management
Even the best security plans will need to adapt as they come under effective targeting. Common threats across on-premises and cloud environments pose varying and similar challenges to administrators attempting to secure the identity and access of legitimate users and must be understood in order to build effective mitigations into solutions. Some of these common threats include:
- Poor policy implementation, especially conditional access
- Absence or misconfiguration of IDAM lifecycle
- Exposed credentials
- Shared accounts
- Improperly configured or overly permissive permissions
- Excessive privileges
- Lack of appropriate monitoring and alerting
- IT environment misconfigurations
Considering the threats posed by poor management, there are a number of abuses possible by authorised and unauthorised users. Considering the approach to these threats should involve reviewing the current users in your environment, what users can do within and outside of the business, and how behaviour is managed to prevent negative impacts.
Get started with identity and access management
It can be overwhelming knowing where to start with IDAM, even more so if you already have technical debt. Get in touch with our experts to find out how you can bring value from business security to ensure you understand your tech, and how new solutions can help you towards a better approach to identity and access management.


















